NahamCon CTF 2023 - Hidden Figures
Info
| Name | Difficulty | Author |
|---|---|---|
| Hidden Figures | Easy | JohnHammond |
Look at this fan page I made for the Hidden Figures movie and website! Not everything is what it seems!
Recon
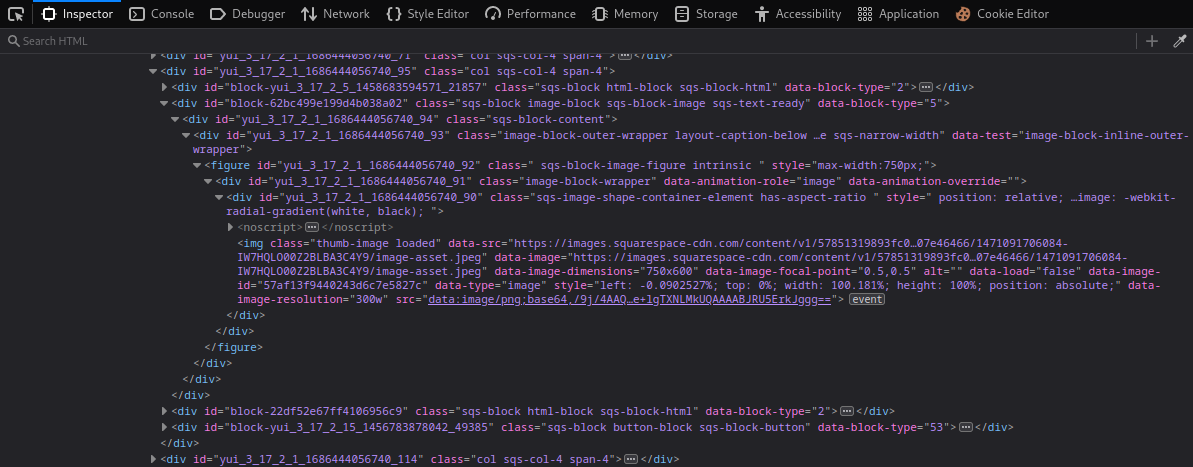
When we enter the page we find a static page with nothing but images, text and a weird javascript file.
The most striking thing is that all the images are loaded through a bunch of base64 code.
Extracting the Flag
CyberChef
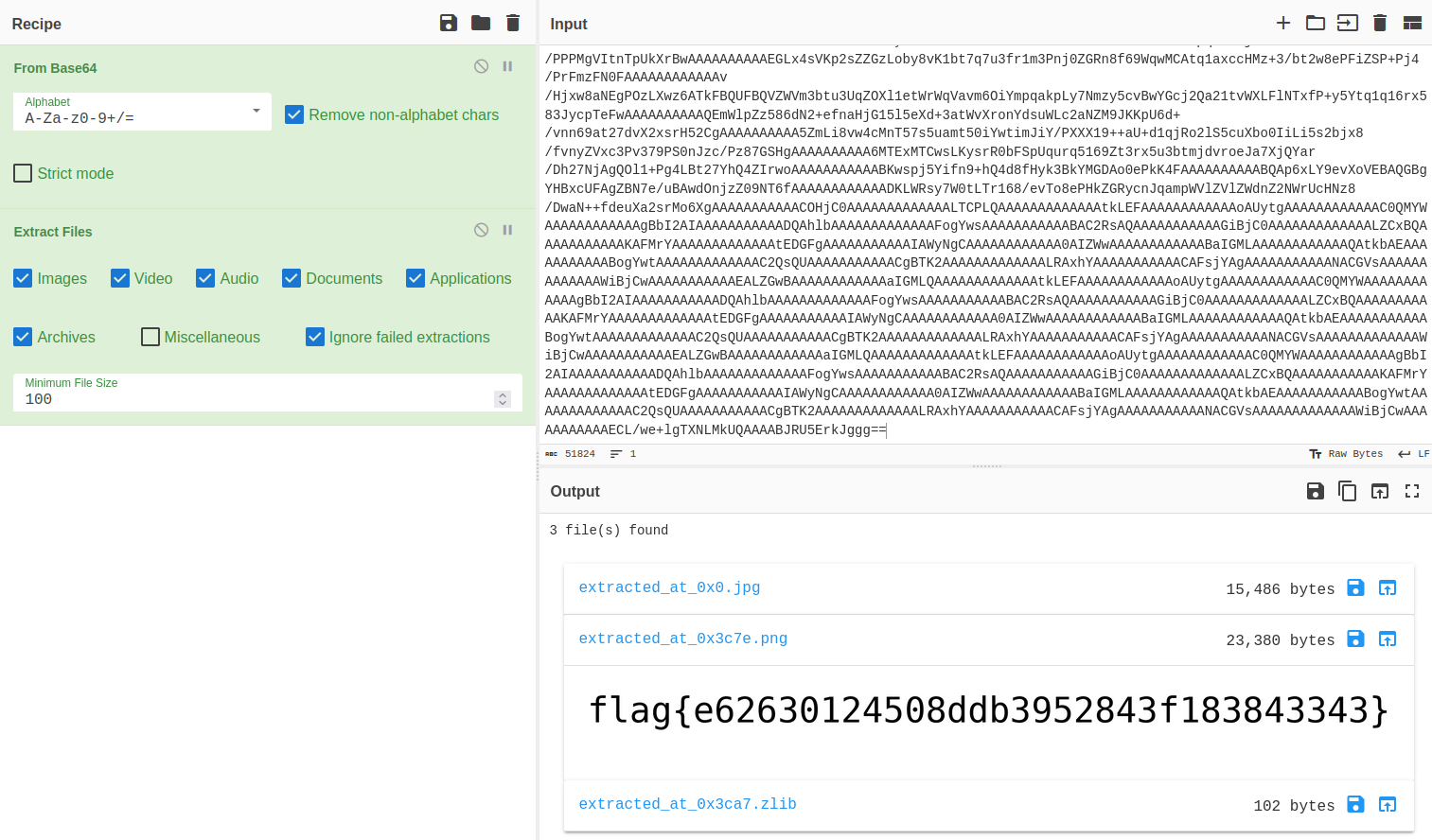
After looking around and not seeing anything else suspicious apart from the base64, let’s see if we can extract anything from it using CyberChef.
Perfect! one of the images contained the flag.
Binwalk
Before trying the extraction with CyberChef, I tried with binwalk -e without any result, so far I am not sure why it could be, maybe the embedded file might be fragmented or stored in a non-contiguous manner within the input file.
But with this other way of using binwalk, we can successfully extract the flag just like with CyberChef.
1
2
3
4
5
6
7
8
9
10
$ binwalk -D=".*" image.jpeg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
15486 0x3C7E PNG image, 1851 x 174, 8-bit/color RGB, non-interlaced
15527 0x3CA7 Zlib compressed data, default compression
$ file 3C7E
3C7E: PNG image data, 1851 x 174, 8-bit/color RGB, non-interlaced
Final Thoughts
It was not a bad challenge, but I was expecting something more web, it was really a steganography challenge, but I learned more binwalk options and how to extract files with CyberChef.